Cybersecurity
Cybersecurity
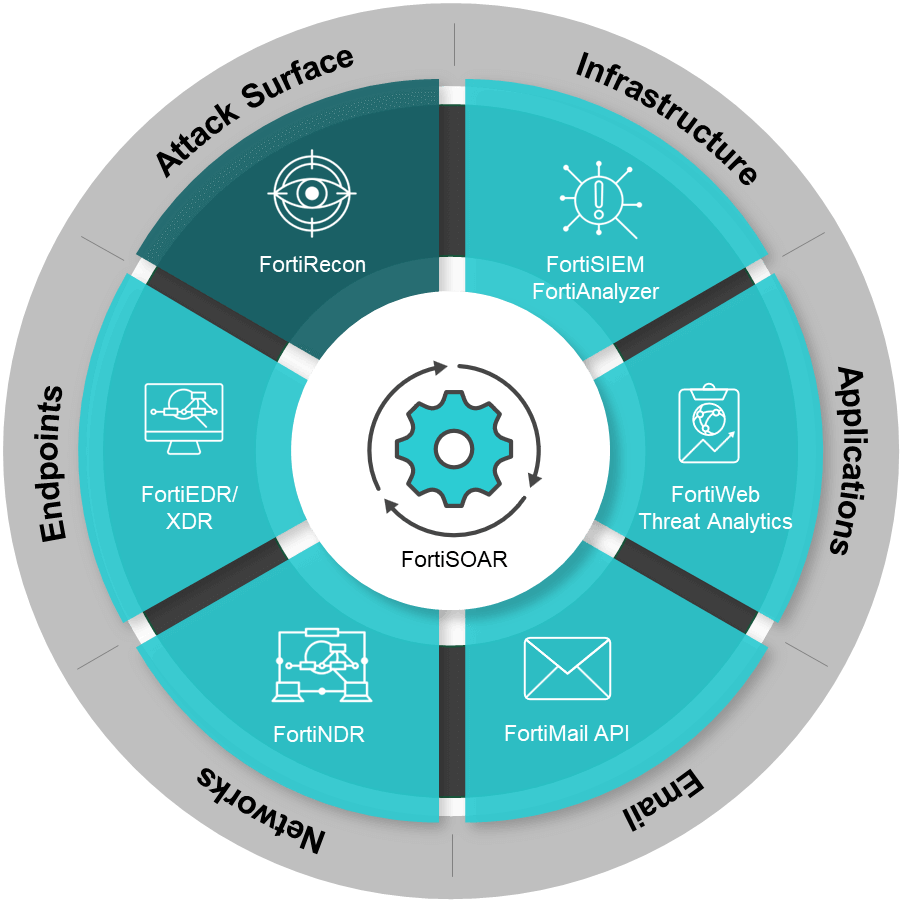
Comprehensive security solutions to safeguard data and systems from cyber threats. Conducting thorough assessments to identify vulnerabilities and potential threats within IT infrastructure. Securing endpoints such as devices and servers to prevent malware infections and unauthorized access. Ensuring regulatory compliance and managing cybersecurity risks effectively to maintain business continuity. We use Penetration Testing by a simulated attack to check for vulnerabilities. The test tries to breach your APIs and servers to find exploitable weaknesses, and vulnerabilities in networks, web applications, or people, a vulnerability assessment reviews security weaknesses in an information system. First, the test assesses whether the system is vulnerable to known security issues. The evaluation then assigns severity levels to the vulnerabilities and recommends mitigation. Threats the assessment prevents include SQL and code injections and insecure defaults., Incident Response service prevents attacks before they happen. As a result, you experience reduced business disruption resulting from cyberattacks. You also reduce regulatory fines, lost revenue, and other costs of cyberattacks, and cyber threat intelligence that gathers, processes, and analyses data to better understand a potential danger to prevent data loss and provide guidelines about safety measures.
Understanding the a Cybersecurity
Cybersecurity refers to the protection of computer systems, networks, and data from cyber threats such as hacking, malware, ransomware, and phishing attacks. It involves implementing a combination of technologies, processes, and practices to defend against threats, detect vulnerabilities, and respond to incidents. Cybersecurity encompasses various aspects, including network security, information security, application security, and operational security. Key components of cybersecurity include firewalls, encryption, intrusion detection systems, antivirus software, and regular security assessments. The goal is to ensure the confidentiality, integrity, and availability of information and systems.
Why Choose a Cybersecurity?
- Protects Sensitive Information: Cybersecurity measures safeguard personal, financial, and proprietary information from unauthorized access and theft, protecting individuals and organizations from data breaches and identity theft.
- Maintains Operational Integrity: Effective cybersecurity helps ensure that critical systems and operations are not disrupted by cyber attacks, minimizing downtime and maintaining business continuity.
- Prevents Financial Loss: By preventing data breaches, ransomware attacks, and other cyber threats, cybersecurity helps avoid costly financial losses associated with recovery, legal penalties, and reputational damage.
- Enhances Regulatory Compliance: Many industries are subject to strict data protection regulations and standards (such as GDPR, HIPAA, and PCI-DSS). Implementing cybersecurity measures helps organizations comply with these requirements and avoid legal repercussions.
- Builds Trust and Reputation: Demonstrating a commitment to cybersecurity fosters trust among customers, partners, and stakeholders, enhancing the organization's reputation and credibility.
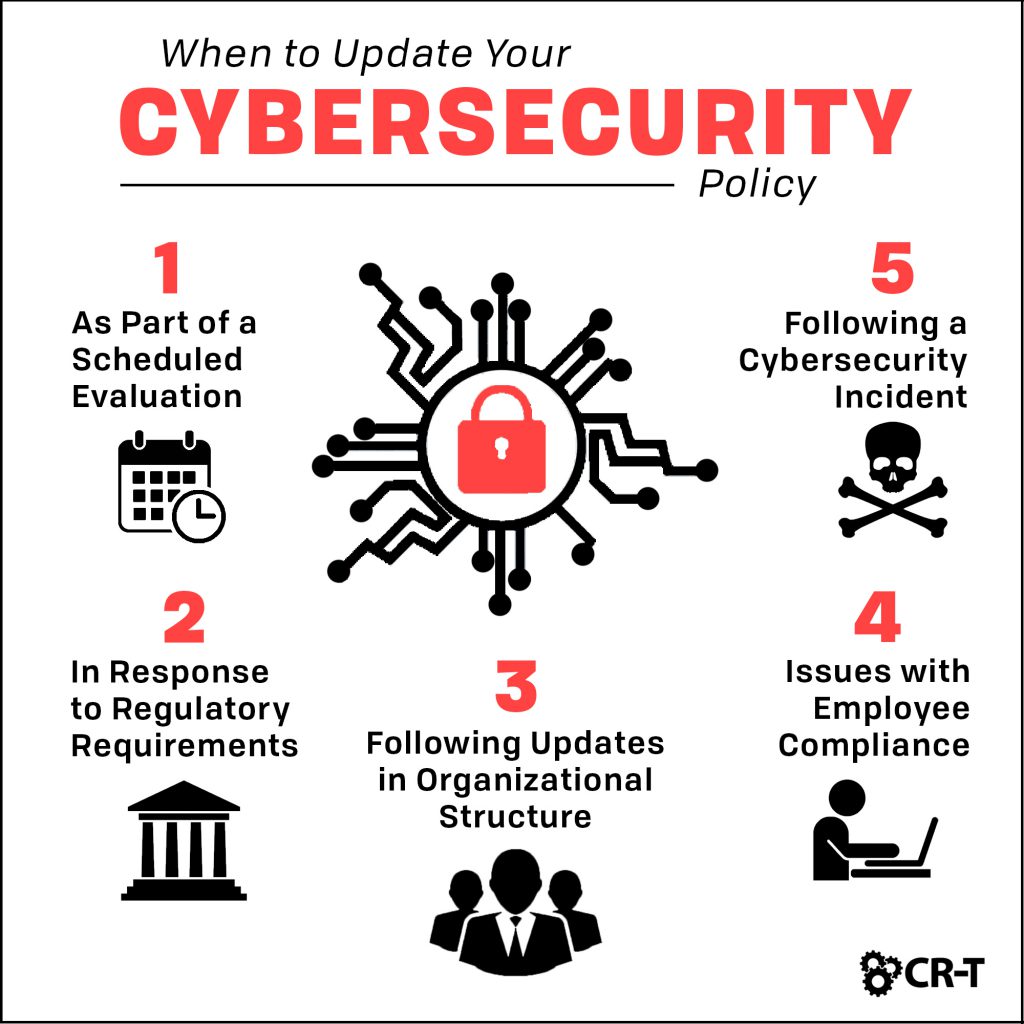
- Adapts to Evolving Threats: Cybersecurity solutions are continuously updated to address emerging threats and vulnerabilities, ensuring ongoing protection against the latest cyber risks and attack vectors.